CYBER-ATTACKS: MOTIVATIONS, METHODS AND MITIGATION
By Mia Borgese
What would you do if someone with malicious intent got access to all your personal details? How about your bank account?
With the increasing amount of important data that we are putting on the internet and storing digitally, with it the number of people trying to gain access to it is increasing. Because of this, the need for people working in cybersecurity is very high and the need for ways to secure data safely is very great.
A common method of attacking is Distributed Denial of Service (DDoS) Attack. This prevents users from accessing a website by maliciously putting a lot of unwanted traffic through it, using multiple computers.
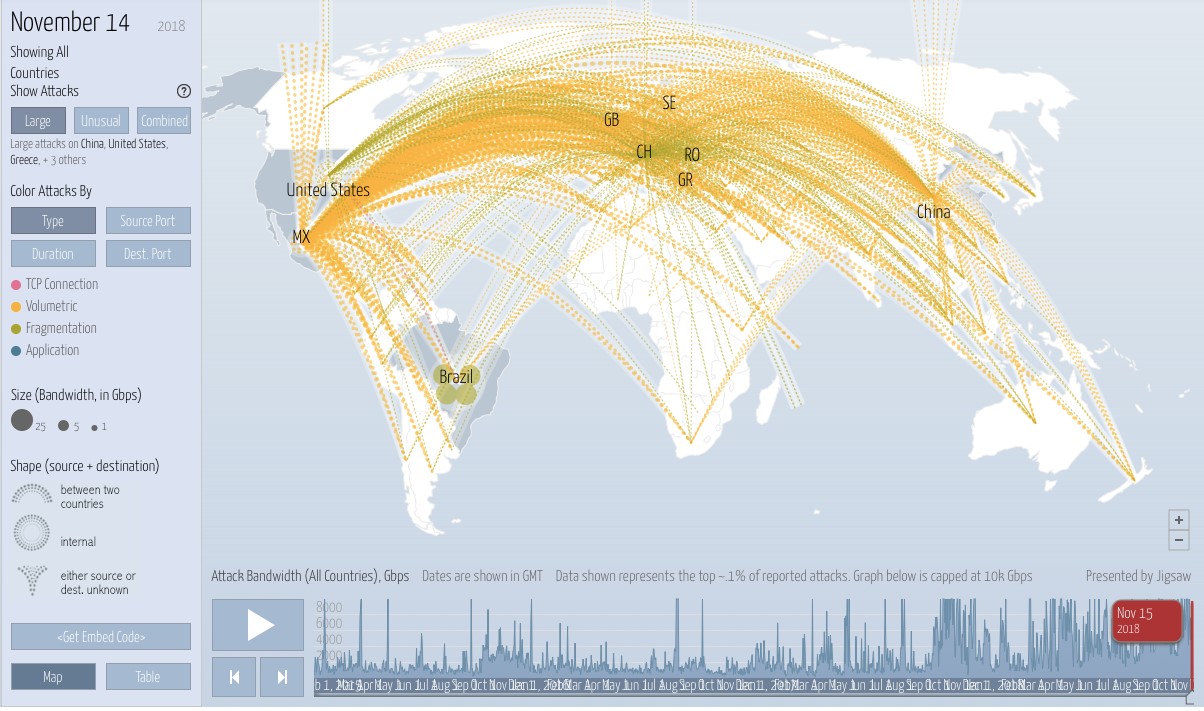
This is a screenshot from the website ‘Digital Attack Maps’ which shows worldwide cyber-attacks in live time:
Many of them may be ‘honeypot’ attacks – harmless or ‘fake’ attacks used as distractions.
Groups of Hackers & Motivations
There are many different groups of people who may want to hack, each of whom with different motivations:
· Black Hat Hackers - illegal
o Financial Gain – people can sell your data or use it to directly get money from you e.g. get into your bank account
o Personal Revenge – people may have vengeance for a person in particular and use their online identity to cause them grief.
o Driven by Politics
o Prestige
o Fun! – there are many people, for example young teenagers, who, for example from their bedrooms, hack into large databases just to see if they can.
· White Hat Hackers – ethical
o To test the security level of a system; usually employed to do so.
Methods of Cyber-Attacking
There are many forms of hacking, but here are, in my opinion, three of the most interesting ones:
1. Password-Cracking (Brute Force Attack)
In this method, the attacker submits as many passwords as needed until the correct one is found. There are many sources which aid this including:
è Dictionary – only helps with single words, sometimes double and triple.
è Rainbow Tables
è Common Password Lists
Password Manager v.s. YubiKey debate
Password-cracking is made much easier by the fact that many people cannot remember all their passwords and so store them digitally on a password manager. They can store a password to any website, or a YubiKey which is a hardware authentication device, similar in method of use to a USB.
2. Biometrics: This is using a biological factor of a person such as fingerprint or iris pattern to authenticate someone and so, give them appropriate access rights.
· This is a good example into the world of computing and biology.
· Despite of the incredible advancements, this method has its flaws. An example of how this can be exploited is the ‘Gummy Bear Attack’. Discovered by Japanese cryptographer Tsutomu Matsumoto, gelatine, as found in a Gummy Bear, and some putty can be used to recreate a human fingerprint which can fool fingerprint security systems.
· They are also flawed because you cannot change your biological factors such as your fingerprint like you can a password . This could pose problems if an account is hacked because someone could replicate your biometric password.
· CRISPR is a coding language which is used to create biometric things e.g. proteins. This can be used to combat many of the problems with biometric cybersecurity measures.
3. Phishing (Social Engineering): When someone fraudulently obtains your information by tricking you into giving it away by pretending to be from a trusted source e.g. by sending an email with a fake link which will download malware or pretending to be an old friend asking for money.
For example, this is an email from someone pretending to be from Bank of America, asking users to follow a link, which may well lead to malware (malicious software) being downloaded onto the victim’s computer, which can be used to destroy the system or obtain sensitive information.
It can be classified as ‘pharming’ attack (which is a type of phishing), as it contains a fake website.
A tell-tale sign of this being an attempt a cyber-attack is its lack of personalisation – but this does not apply to all phishing attempts:
Spear Phishing scams are a lot more difficult to detect as they are heavily personalised. Emails can be customised with the victim’s name, for example, so they are much more easily tricked into believing the email is trustworthy.
Protection Against Hacking
There are so many ways, and it is important that you have at least two methods in place. Here are some examples:
Firewall: filters the traffic that can enter a network
Encryption: turns text into a form that cannot be understood unless someone has the key. Examples include:
o Symmetric Encryption
o Asymmetric Encryption
o Hash Functions (used by banks)